Avoid getting hacked 102: A guide to securing mobile devices

Editor's note: This post is a continuation of our series on how to "avoid getting hacked". Read the first part about secure passwords.
Smartphones like other computing devices contain a lot of important and sensitive information, this makes them appealing to hackers and criminals.
One in every two people reading this article would do so on a mobile device, mobile devices have become such a huge part of our lives. According to datareportal, there are 5.112 billion unique mobile users in the world and 67% of those are smartphone users.
The portability and increasing capabilities of a mobile device makes it a top choice for a computing device. However, every new innovation introduces with it points of exploitation—vulnerabilities—and mobile is not insulated against such.
So, this article aims to reduce the threat associated with using a smartphone in today’s connected society by advising you on how to secure same. This message becomes increasingly important, in the wake of the US, China trade war; where Huawei devices have been accused of using spyware (defined below) to spy on the US for the benefit of their Government. Although, OEM-installed spyware is harder to guide against, the seven tips below would provide a decent introduction to mobile phone security;
7 Tips for securing your mobile devices
These seven tips would instruct you on how to protect your mobile devices from hackers, cybercriminals and the government alike.
- Install Mobile Antivirus
Mobile phones are computing devices and are also susceptible to different kinds of malware, adware, ransomware or spyware. iOS devices are generally more secure than their Android counterparts against malware and viruses.
OEM (Apple) makes software (iOS) that goes on to their mobile devices, and Apple fully vets applications from developers over a 9-12 day period before they let it onto the app store to prevent malware infections. Essentially, Apple operates a "walled garden" policy that helps improve the security of its devices, unlike Android, where Google publishes applications first before a quality assurance team gets to vet the application whenever they come across it.
Android is open-source (see: AOSP) and it provides developers with access to various API's, hackers could abuse the API to create malware that would be harder to detect. Therefore, making it more susceptible to malware infections than their iOS counterparts. Following Apple's logic above, it's easy to imagine how a Google-made smartphone would be more secure than the average android smartphone made by other OEMs.
Smartphone malware includes:
- Adware: This is the most popular form of smartphone malware, it is based on a program that displays unwanted advertisements on your mobile devices. Hackers hide adware in other applications that they disguise as legitimate.
- Ransomware: This is a type of malware that locks access to victims' phones and encrypts their data. Typically, the hackers request for a ransom (payment) in the form of cryptocurrencies such as bitcoin to protect their identity. For example.
- Malicious Cryptomining: This type of malware uses the resources of the victims' device to mine cryptocurrency like bitcoins, the attackers then send the currency to their account. This malware type exhausts the computing resources of the mobile phone, draining the battery or causing it to overheat.
- Spyware: This type of malware is used by attackers to secretly obtain information or observe the victim and report back to the Hacker. This is what Trump is accusing smartphone maker Huawei of doing for China—using their devices to spy on the US and report back to China.
Mobile malware is designed to stay hidden apart from the likes of a ransomware, where the hacker needs you to know so you can pay the ransom. It is advisable to use a mobile antivirus to scan your device routinely for any traces of malware or applications misusing their permissions.
Suggested antivirus software for Android devices are Malwarebytes and ESET Mobile Antivirus.
2. Always update your applications and operating system.
Our mobile phones are usually filled with several applications; from social media to e-commerce and lifestyle/banking applications. Keeping our devices and information secure can be as easy as updating these applications whenever an update is released—as most updates come with bug fixes and security patches.

Most recently a vulnerability was found on WhatsApp messaging platform that allowed hackers to install spyware on a device by placing a WhatsApp call to the device. After this vulnerability was found, Facebook (owners of WhatsApp) released an update the next day to remedy the situation. Applications and OS developers regularly release updates to fix both bugs and critical security issues, and we as users should ensure we update our mobile devices whenever we see an update available.
Also, users should buy devices from trusted manufacturers that have a history of releasing regular updates for their devices (untrusted device brands aren't advised) and where possible turn on “Auto Updates" for your apps.
3. Turn off your Bluetooth when it is not in use
Those relatives that cautioned us to turn off Bluetooth to prevent our phones from being infected with viruses when we were younger weren't far from the truth, Bluetooth is a wireless technology and therefore it is inherently susceptible to remote access or spying by hackers.
Bluetooth offers various security authentication, but we frequently hear of a new Bluetooth vulnerability that allows hackers to remotely access our devices, examples are:
- Car Whisperer: This is a software that allows attackers to remotely connect to our Bluetooth-enabled car stereo sets and play audio or listen to the audio.
- Bluebugging: This was a vulnerability that allowed hackers to remotely control our devices and use their features via Bluetooth bypass authorisation.
- Blueborne: This was a vulnerability that allowed hackers to remotely attack Bluetooth devices and bypass authentication, and in certain scenarios devices that weren't even discoverable.
The listed vulnerabilities have been patched by all major OEMs but research shows that 2 billion devices are still exposed to the blueborne vulnerability. Therefore, as users, we should ensure to turn to our Bluetooth devices when they aren't in use to reduce the chance of remote attacks via Bluetooth.
4. Limit your use of free/unsecured WiFi networks
That free wifi network at your favourite cafe/store, avoid it. Unsecured WiFi networks are basically open season for hackers, they could execute MITM attacks: this is an attack type where the hacker positions themselves in between the user and the wifi router.

This is done so the attacker can intercept the user traffic before it gets to the router, this basically gives the hackers access to all the information you send on the network. Hackers can also send malicious information in an attempt to install malware or spyware on your mobile device.
If and only if you really have to make use of public/unsecured wifi networks, ensure you use a VPN.
5. Do not jailbreak (iOS) or root (Android) your devices unless you have a specific reason
Most advanced mobile users jailbreak or root their devices to enable features that were previously disabled by the OEMs to grant them full access to the operating system of the phone. Unlocking your phone grants you administrative access to the mobile OS and that access could be misused if you aren't careful or an advanced user.
Unlocking your device compromises the security model of your device to the point that most banking applications won't run on an "unlocked" device. OEMs do not support unlocked devices, so users of unlocked devices have to look towards 3rd party developers for updates to their devices.
Due to the fact that unlocking a device grants the user administrative access to the device, any malware or viruses present on the device could also access and use these admin privileges. Unlocking your device gives you access to previously locked features, but the drawbacks and risk associated for any user that values device security outweigh the pros.
6. Never install unknown applications from outside your app store
Installing applications from unknown sources is a major security risk, it is almost impossible for any user to guarantee the legitimacy of an application that is downloaded from a third-party source. While the app store isn't guaranteed to be void of malware, it is still a much safer option than third-party applications.
Applications from outside the app store could be infected with backdoor malware that grants an attacker remote access to your device.
7. Encrypt your Device backup
Our phones have become a huge part of our lives and contain sensitive information, various factors necessitate the need for regular backups, from theft, hardware failure or even a malicious attack by a hacker. It is important to regularly backup our devices to ensure that we do not lose our information.
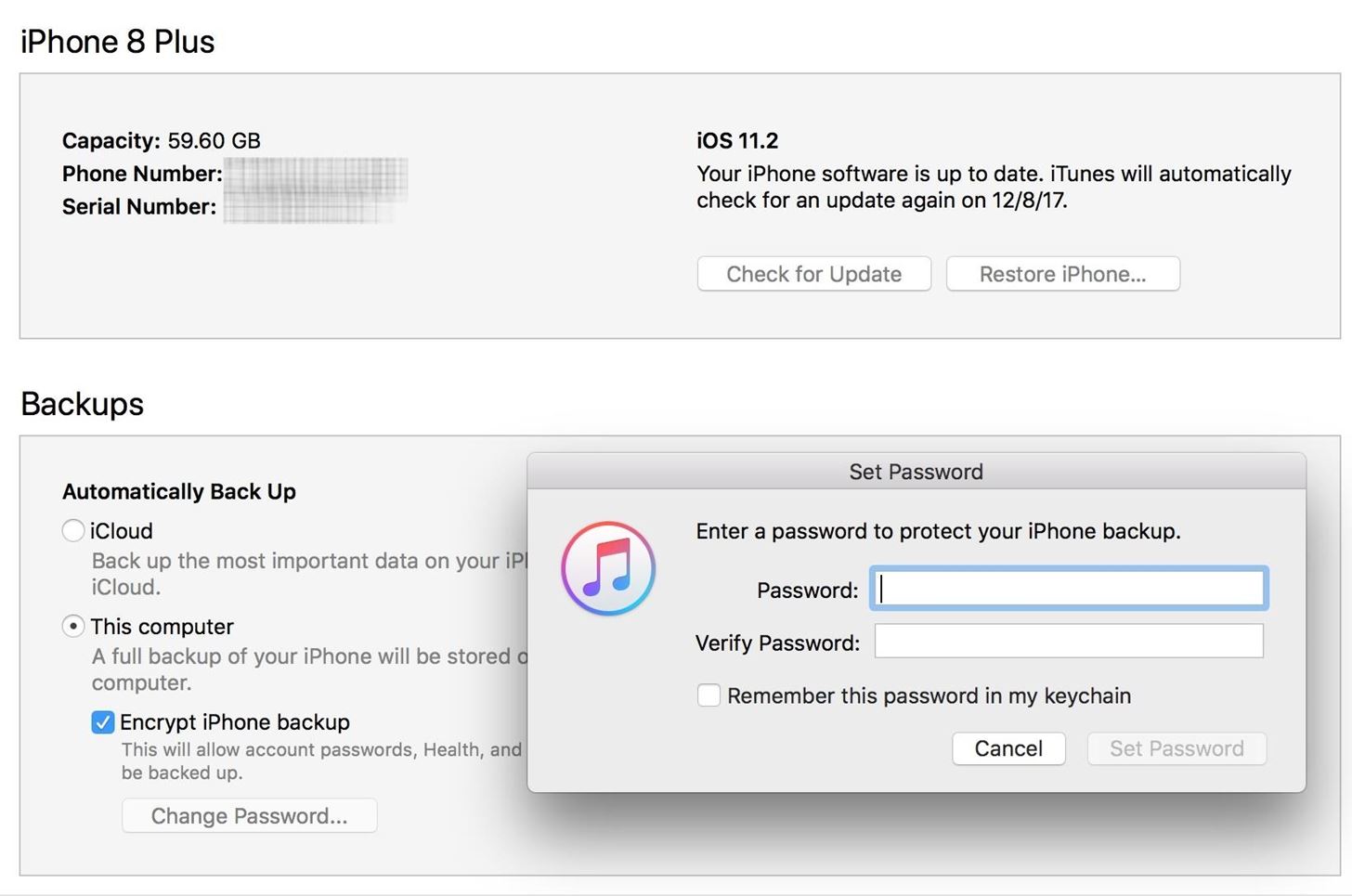
These backups could be to cloud-based servers like iCloud, Google Drive or local devices like our computers and storage devices when backing up data to local devices ensure that your backup is password protected so as to reduce the chances of hackers exfiltrating our information from the backup.
Do you have any other suggestions on how to secure a mobile device? We want to hear from you. Hit us up on Twitter: @dadabenblog.






